Bot Herders Activities Include Which of the Following
34 Cyber criminals gain information on a victim by monitoring online activities accessing databases and so on and make false accusations that damage the reputation of the victim on blogs Web sites chat rooms or e- commerce sites. Bot herders may also be bot masters in which case they use the compromised systems for various types of cyber activities such as conducting distributed denial of service DDOS attacks running click fraud.

Bot Botnet Bot Herder And Bot Master Cyberhoot
Bot herder D cyber-robot.
.png)
. Many channels support the ability for a bot or user to mention someone within the context of a conversation. Which of the following would disallow virus circulation. To mention a user in a message populate the messages.
The word botnet is a portmanteau of the words robot. Once theyve compiled the bots a herder uses command programming to drive their next actions. Which of the following information security controls creates an appealing isolated environment for hackers to prevent them from compromising critical targets while simultaneously gathering information about the hacker.
Recent Examples on the Web The bot herder can continue to remotely manage and grow their botnet to carry out various malicious activities. 426 62 Which of the following terms refers to a computer data or network site that is designed to be enticing to crackers so as to detect deflect or counteract illegal activity. Which of the following was introduced in 2011 to increase the participation of all stakeholders in emergency management activities.
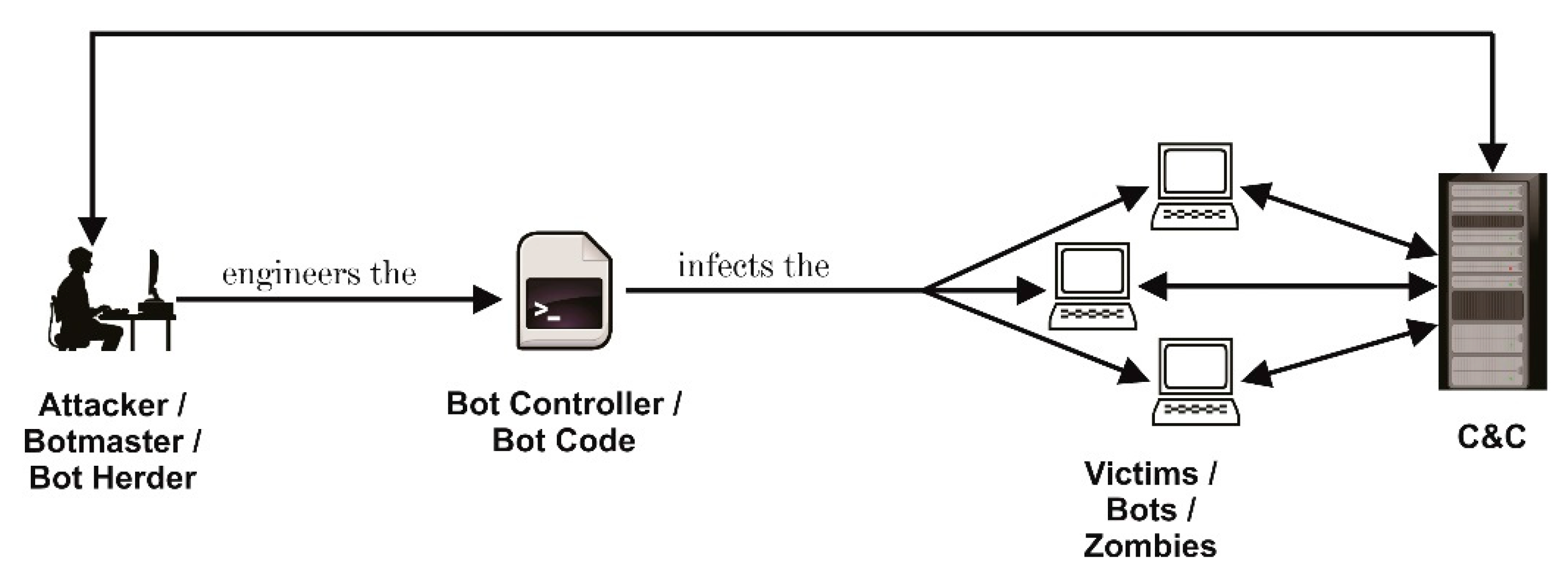
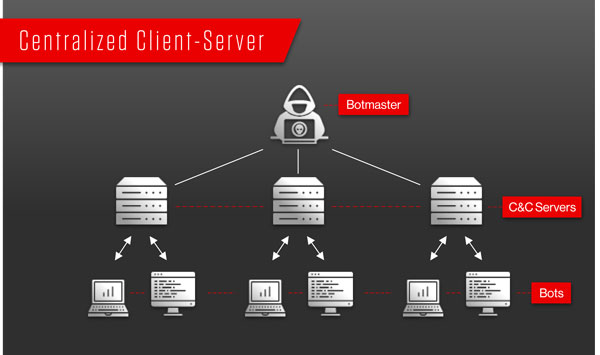
This could include distributing spam to the email contact addresses on each zombie computer for example. Bot Roast is an operation by the FBI to track down bot herders crackers or virus coders who install malicious software on computers through the Internet without the owners knowledge which turns the computer into a zombie computer that then sends out spam to other computers from the compromised computer making a botnet or network of bot. The botnet is under the command of a bot herder or a bot master usually to perform nefarious activities.
Include the design and development of applications that support the primary business activities. To control the machines in the network the bots are infected with malware that places them under the control of the bot herder. Individual hosts in a Botnet are known as bots or zombies.
Juan a cybersecurity expert has been hired by an organization whose networks have been compromised by a malware attack. Each individual machine under the control of the bot. In the order-to-cash process checking credit is followed by ________.
Infected computers and other systems within the botnet are called zombies systems which are controlled by bot programs that allow the bot-herders to perform all operations from a remote location. Bot herders use botnets for a variety of different purposes including. B creating an order.
The administrator of the Botnet is often known as a Bot Herder. D Bot herding. A few examples of Botnets include.
A Oligomorphic malware B Use of an MSC file C Use of a screen saver file D. The bot herder acts remotely sending updates to infected machines manipulating their actions as. Human resource activities _____.
E Spam filtering. A disaster response communication plan should include protocols for which of the following. Bot herders can direct each of the zombies in the botnet to launch DoS attacks against any target.
The following procedure is intended to provide guidance and direction in determining how TTBIA. Spam _____ costs are ongoing costs that occur throughout the life of the system. A honeypot B firewall C bot herder D botnet E zombie computer A honeypot.
A botnet is a number of Internet-connected devices each of which runs one or more botsBotnets can be used to perform Distributed Denial-of-Service DDoS attacks steal data send spam and allow the attacker to access the device and its connectionThe owner can control the botnet using command and control CC software. Which of the following is true of system effectiveness. Infected bots are often referred to as zombies.
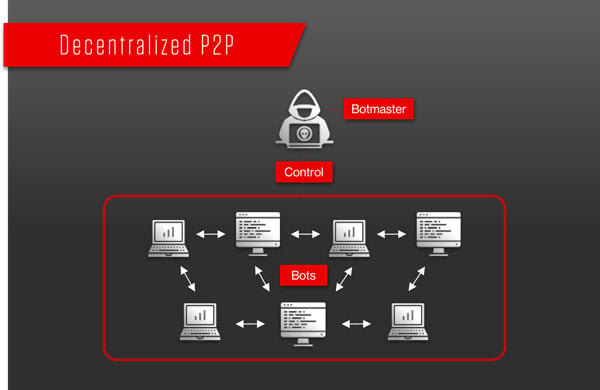
What social engineering attack has Michelle performed. A bot herder is a hacker that seeks out vulnerable computers and infects them so that they can be controlled as a botnet. Nowadays most botnets rely on existing _____ networks for communication.
Michelle pretends to be the help desk manager and calls Steve to trick him into giving her his password. Botnets are a collection of compromised computers that can be sent orders to each others. The bot herder can then command all bots to do its bidding which is typically to carry out attacks.
After analyzing the network systems Juan submits a report to the company mentioning that the devices are infected with malware that uses a split infection technique on files. Botnet Option 3. When these botnet zombies attack a system its a Distributed DoS DDoS attack.
The meaning of HERDER is one that herds. Storm Krakenand Conficker Typically refers to botnets used for illegal purposes. Intrusion detection system Option 4.
The party taking command duties may have set up the botnet or be operating it as a rental. A server-to-server b peer-to-peer c client-to-server d host-to-server View. A bot is a piece of malware that infects a computer to carry out commands under the remote control of the attacker.
Each of the individual systems in the botnet can be directed to send. A person who manages breeds or tends to livestock. Honeypot Option 2.
A botnet short for robot network is a network of computers infected by malware that are under the control of a single attacking party known as the bot-herder. Negotiate price and terms. With savvy bot herders taking down command-and-control servers regularly to avoid detection security specialists have to update the list of known rogue servers dynamically and in real time Geyer.
A bot herder leads a collective of hijacked devices with remote commands. Which of the following is considered one of the most destructive and difficult cyberthreats to prevent. Denial of service DoS attacks.
Information Free Full Text A Botnets Circumspection The Current Threat Landscape And What We Know So Far Html
Comments
Post a Comment